Security and safety have long been two different technical fields with little relation to each other. Security on one hand has been mostly related to either malicious stealing of computer system data (hacks) or unintentional mistakes when dealing with confidential data. The main focus of safety and in particular “functional safety” on the other hand has been on the unintentional technical failure of electric/electronic systems, e.g. a break of cables or human errors at design time of a system. Whereas security has been mostly relevant in the IT world, functional safety has had its stronghold in industrial domains for engineering of machines.
These paradigms have changed recently when safe systems got connected to the outside world. Safe systems suddenly became attackable. Even though most consumer IoT devices are not safety-relevant, first effects are already visible. Examples are recent hacks of connected cars, where hackers even were able to threaten people by accessing the car brakes. It is evident that a rethinking must take place and new systems must be designed in a new way.
AT&T observed a 458% increase in IoT hacks the last two years. In SCOTT we focus on IoT applications for e.g. vehicles, airplanes and rail and the intention is to cover a broad spectrum of typical IoT devices, from home environment, to automotive towards more industrial airplanes and railway with highest safety and security standards. While the unavailability of the Internet or a cellular network may result in some annoyed users and lost productivity, a large scale compromise of IoT devices may lead to loss of lives and large scale user impacts.
Since IoT devices cover such a wide range, SCOTT does not try to find one all-encompassing solution that fits all, but our objective is to identify key needs for each IoT application that we have in the consortium, harmonize commonalities and leave room for specific needs e.g. airplanes. The high-level objective of this project is to secure IoT devices and justify the trust the users put into them.
The objective of this Technology Line is to find solutions or extend existing solutions for IoT security and safety.
In particular, the Technology Line will implement or provide:
This will be implemented and demonstrated in WP23.
The achieved privacy and security has to be quantified to avoid home-cooked security approaches. This is of special importance for IoT where some IoT devices may be connected for 20 years and robust security is essential. We will focus in our project on wireless communication, but therein take several access possibilities into account.
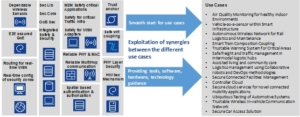
The objectives of SCOTT in terms of measureable indicators are (see also Figure):
The delivery of the building blocks can be measured. They are either software or reports/guidelines. The high level main objective is that they will enable the different use case and provide synergies inside the project of at least 20%-30%.
